UN Cyber norms
Cyber norms are voluntary guidelines and principles that promote responsible state behaviour in cyberspace. They are designed to enhance international security and stability by providing a framework for states and other stakeholders to follow in order to mitigate cyber threats and prevent cyber conflicts.
The set of 11 voluntary, non-binding cyber norms were first developed in 2015 and agreed within the United Nations Groups of Governmental Experts (GGE) and later reaffirmed by all UN Member States in the Open-Ended Working Group (OEWG) processes.
As a part of the UN framework of responsible state behaviour, these norms include respecting international law, protecting critical infrastructure, refraining from malicious activities such as cyber espionage and electoral interference, and ensuring due diligence to prevent non-state actors from using a state’s territory or ICT infrastructure for wrongful acts.
Although non-binding, these norms are intended to build cooperation, transparency, and trust among states and other actors in the digital environment. Yet, their implementation remains a constant challenge, requiring sustained dialogue, technical cooperation, and mechanisms to address violations. At the same time, differences persist among states—some argue that the existing framework is sufficient if fully implemented, while others advocate for the development of additional norms, including the possibility of new binding obligations to strengthen accountability.
The Final Report of the OEWG 2021-2025 sets up a new single track permanent mechanism called ‘Global Mechanism on developments in the field of ICTs in the context of international security and advancing responsible State behaviour in the use of ICTs’ that will continue discussions about five pillars of the framework, including the implementation of the agreed cyber norms.
In parallel, a range of multistakeholder initiatives address the practical implementation of the norms, engaging non-state actors such as the private sector, academia, the technical community, and civil society. One such initiative is the Geneva Dialogue on Responsible Behaviour in Cyberspace, whose outcomes and reflections are captured in the Geneva Manual, providing valuable inputs and perspectives on how the norms can be operationalised.
UN Cyber Norms
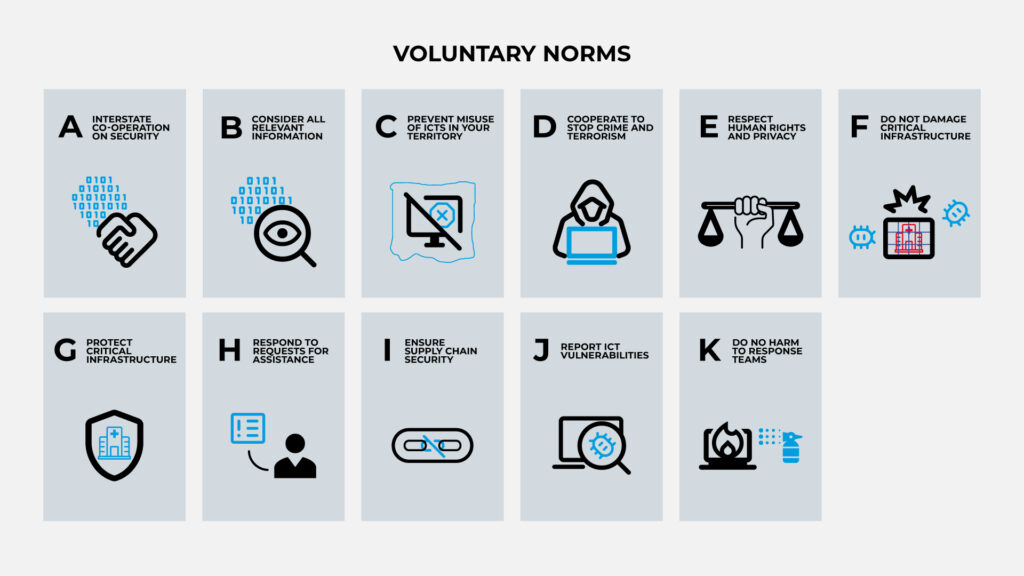
A. Interstate co-operation on security
Consistent with the purposes of the United Nations, including to maintain international peace and security, States should cooperate in developing and applying measures to increase stability and security in the use of ICTs and to prevent ICT practices that are acknowledged to be harmful or that may pose threats to international peace and security.
B. Consider all relevant information
In case of ICT incidents, States should consider all relevant information, including the larger context of the event, the challenges of attribution in the ICT environment and the nature and extent of the consequences.
C. Prevent misuse of ICTs in your territory
States should not knowingly allow their territory to be used for internationally wrongful acts using ICTs.
D. Co-operate to stop crime and terrorism
States should consider how best to cooperate to exchange information, assist each other, prosecute terrorist and criminal use of ICTs and implement other cooperative measures to address such threats. States may need to consider whether new measures need to be developed in this respect.
E. Respect human rights privacy
States, in ensuring the secure use of ICTs, should respect Human Rights Council resolutions 20/8 and 26/13 on the promotion, protection and enjoyment of human rights on the Internet, as well as General Assembly resolutions 68/167 and 69/166 on the right to privacy in the digital age, to guarantee full respect for human rights, including the right to freedom of expression.
F. Do not damage critical infrastructure
A State should not conduct or knowingly support ICT activity contrary to its obligations under international law that intentionally damages critical infrastructure or otherwise impairs the use and operation of critical infrastructure to provide services to the public.
G. Protect critical infrastructure
States should take appropriate measures to protect their critical infrastructure from ICT threats, taking into account General Assembly resolution 58/199 on the creation of a global culture of cybersecurity and the protection of critical information infrastructures, and other relevant resolutions.
H. Respond to requests for assistance
States should respond to appropriate requests for assistance by another State whose critical infrastructure is subject to malicious ICT acts. States should also respond to appropriate requests to mitigate malicious ICT activity aimed at the critical infrastructure of another State emanating from their territory, taking into account due regard for sovereignty.
I. Ensure supply chain security
States should take reasonable steps to ensure the integrity of the supply chain so that end users can have confidence in the security of ICT products. States should seek to prevent the proliferation of malicious ICT tools and techniques and the use of harmful hidden functions.
States should encourage responsible reporting of ICT vulnerabilities and share associated information on
available remedies to such vulnerabilities to limit and possibly eliminate potential threats to ICTs and ICT- dependent infrastructure
K. Do no harm to response teams
States should not conduct or knowingly support activity to harm the information systems of the authorized emergency response teams (sometimes known as computer emergency response teams or cybersecurity incident response teams) of another State. A State should not use authorized emergency response teams to engage in malicious international activity.
