Hacking group APT28 breaches Ukrainian government email servers
Exploiting webmail vulnerabilities, the hackers redirected emails to steal information.

It is alleged that hackers from APT28 linked to Russia’s General Staff Main Intelligence Directorate (GRU) have hacked into the Roundcube email servers belonging to several Ukrainian organisations, including government entities.
It is believed that the hackers took advantage of the current conflict between Russia and Ukraine to trick recipients into opening malicious emails that exploited Roundcube Webmail vulnerabilities and hacked into unpatched servers. Upon compromising the servers, the hackers deployed malicious scripts that redirected the incoming emails of targeted individuals to an email address under their control to steal victims’ address books, session cookies, and other information stored within Roundcube’s database.
According to the joint investigation conducted by Ukraine’s Computer Emergency Response Team (CERT-UA) and Recorded Future’s threat research division Insikt Group. The aim was to harvest and steal military intelligence to support Russia’s invasion of Ukraine, and these attacks had been operational since around November 2021.
The Insikt Group claimed, ‘We identified BlueDelta activity highly likely targeting a regional Ukrainian prosecutor’s office and a central Ukrainian executive authority, as well as reconnaissance activity involving additional Ukrainian government entities and an organisation involved in Ukrainian military aircraft infrastructure upgrade and refurbishment.’ They added, ‘The analysed BlueDelta phishing campaign exploits the vulnerabilities CVE-2020-35730, CVE-2020-12641, and CVE-2021-44026 in the open-source webmail software Roundcube in order to run multiple reconnaissance and exfiltration scripts.’
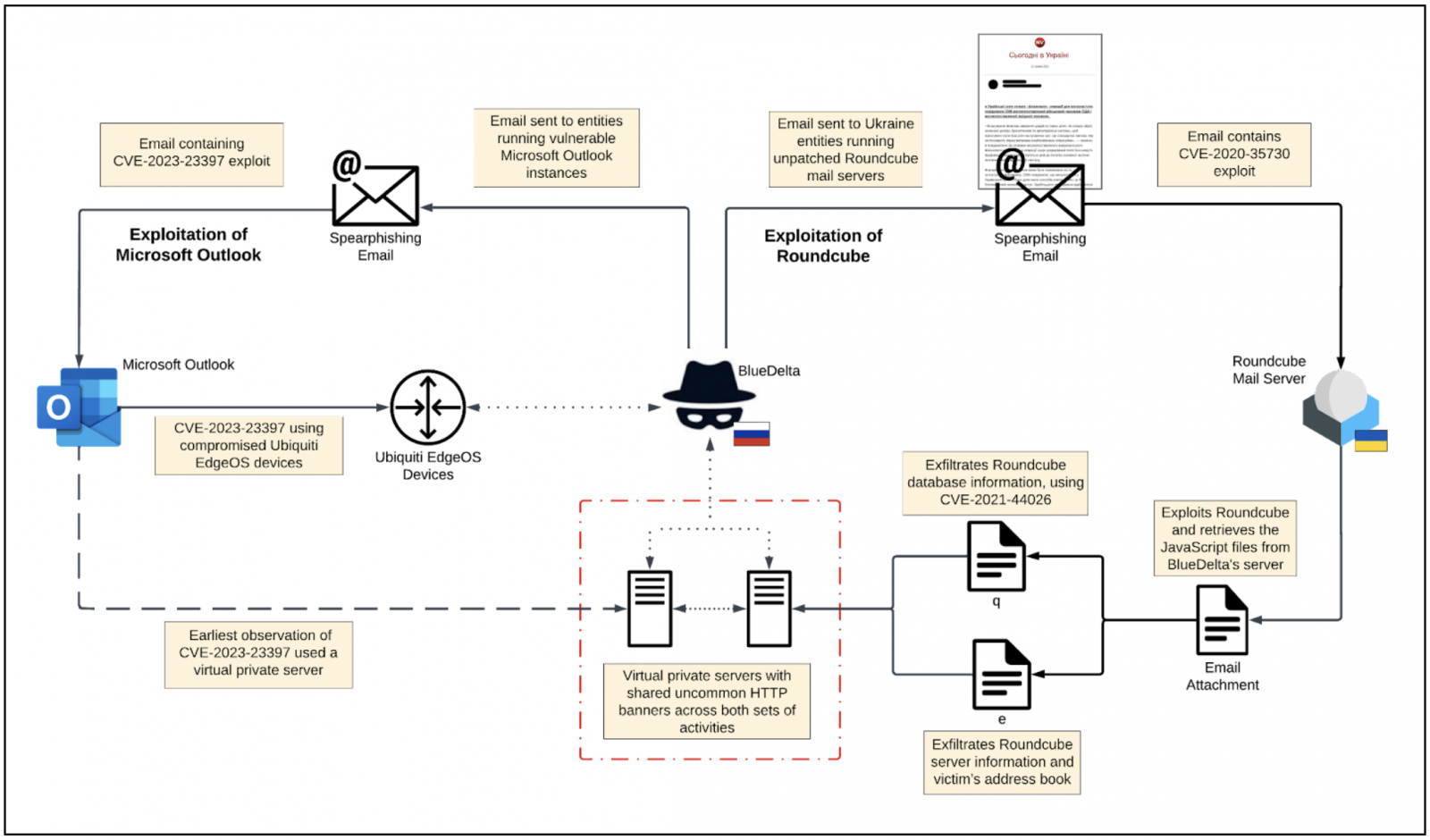
Image: PT28 Outlook and Roundcube activity overlap (Recorded Future’s Insikt Group)
Recorded Future claimed that this campaign overlaps with earlier cyber-espionage campaigns linked to APT28, such as when the hackers exploited a Microsoft Outlook zero-day vulnerability (CVE-2023-23397) to target European organisations.
Google’s Threat Analysis Group reported that roughly 60% of all phishing emails targeted in Ukraine in the first quarter of 2023 were sent by Russian attackers, with APT28 significantly contributing to these activities.
