Cloud computing
Cloud computing caused a shift from storing data on hard disks on our computers to storing it on servers in the cloud. Some examples include your email account which you can access from different devices, and any photos, videos, or documents you store online (even if your account is private).
Cloud computing offers ubiquitous access to all of our data and services from any device anywhere where there is an Internet connection.
The first wave of cloud computing started with the use of online mail servers (Gmail, Yahoo, etc), social media applications (Facebook, Twitter, etc), and online applications (Wikis, blogs, Google docs, etc).
Apart from everyday applications, cloud computing is used extensively for business software. More and more of our digital assets are moving from our hard disks to the cloud. Due to their large server farms, tech giants such as Google, Microsoft, Apple, Amazon, and Facebook are among the main cloud computing players in the private sector.
From hard disks to cloud computing
Today's cloud computing ecosystem is made up of large central computers and server farms, and billions of 'dumb' units in the form of laptops, notebooks, mobile phones, and other devices.
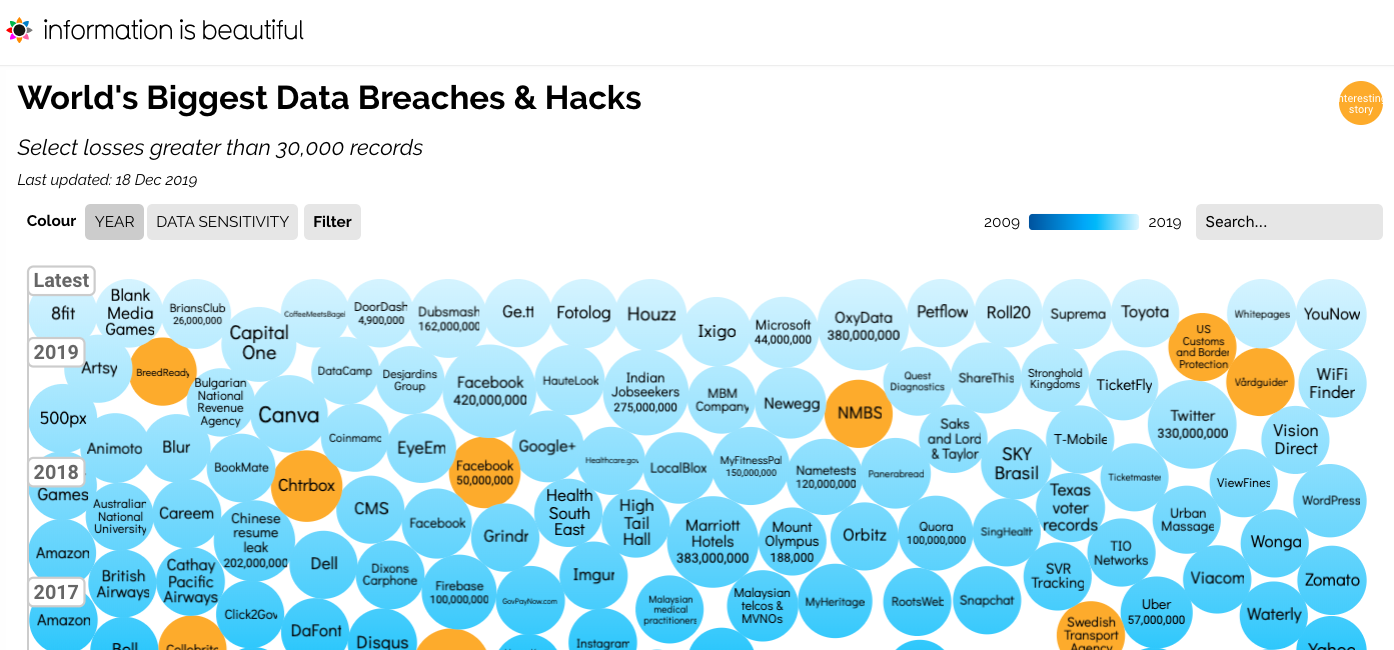
The fact that our data is stored with a third party - often in pieces with copies scattered around several jurisdictions - raises a number of security and privacy concerns. Since each cloud hosts enormous amounts of information and data about users, companies, and other entities, the risks associated with security breaches of any cloud provider carries severe implications.
Since we are effectively dealing with data, many of the issues related to cloud computing are also dealt with in discussions on data governance.
Setting common standards
With a diverse set of operators of cloud computing, the need for standards is - and will remain- important. The adoption of common standards ensures a smooth transfer of data among different clouds. In recent years, the notion of data portability, that is, the right of a user to be able to transfer their data from one service provider to another (for instance, from Google to Apple or vice-versa) has become relevant. The EU's General Data Protection Regulation, which came into effect in May 2018, makes data portability an enforceable right for European citizens.
There are a number of working groups on cloud computing, such as The Open Group Cloud Computing Work Group, which includes some of the industry's leading cloud providers and end-user organisations, as well as the Cloud Computing Strategy Working Group by the European Telecommunications Standards Institute. Other initiatives include Google's Data Liberation Front, which aims at ensuring a smooth transition of data between different clouds.
Securing the cloud
With more services delivered online, modern society will increase its dependence on the Internet. In the past, blocked access to the Internet meant the inability to send e-mails or browse the web. In the era of cloud computing, the implications of 'going dark' are far greater: Complete systems can fail if damage occurs to the cloud. This higher dependence on the Internet implies greater pressure on its robustness and reliability.
The same can be said for data breaches. As the occurrence of breaches increases over time, service providers are faced with increasing pressure to take stronger security measures.
With more of our personal data stored on the cloud, issues such as privacy and data protection are also central to the debate. Who has access to our data, and how is it processed? Since many service providers are based in the USA, the issue affects mainly tech companies in the USA while affecting users worldwide
The Safe Harbour Agreement, which was meant to solve issues related to the existence of differing privacy regimes in the USA and the EU, was declared invalid by the European Court of Justice in October 2015. The agreement was later replaced with a new framework - the EU-US Privacy Shield - which affords a high level of data protection to EU citizens travelling across the Atlantic. The Privacy Shield undergoes regular reviews.
Governing the cloud
With a growing volume of information assets going digital, some countries are uncomfortable with having national information assets outside of their national borders. To alleviate these concerns, these countries have demanded that certain data be stored on national or regional clouds.
These measures have been controversial, as other countries believe that data should flow freely across borders. Once again, issues related to the governance of the cloud are strongly linked to data governance.