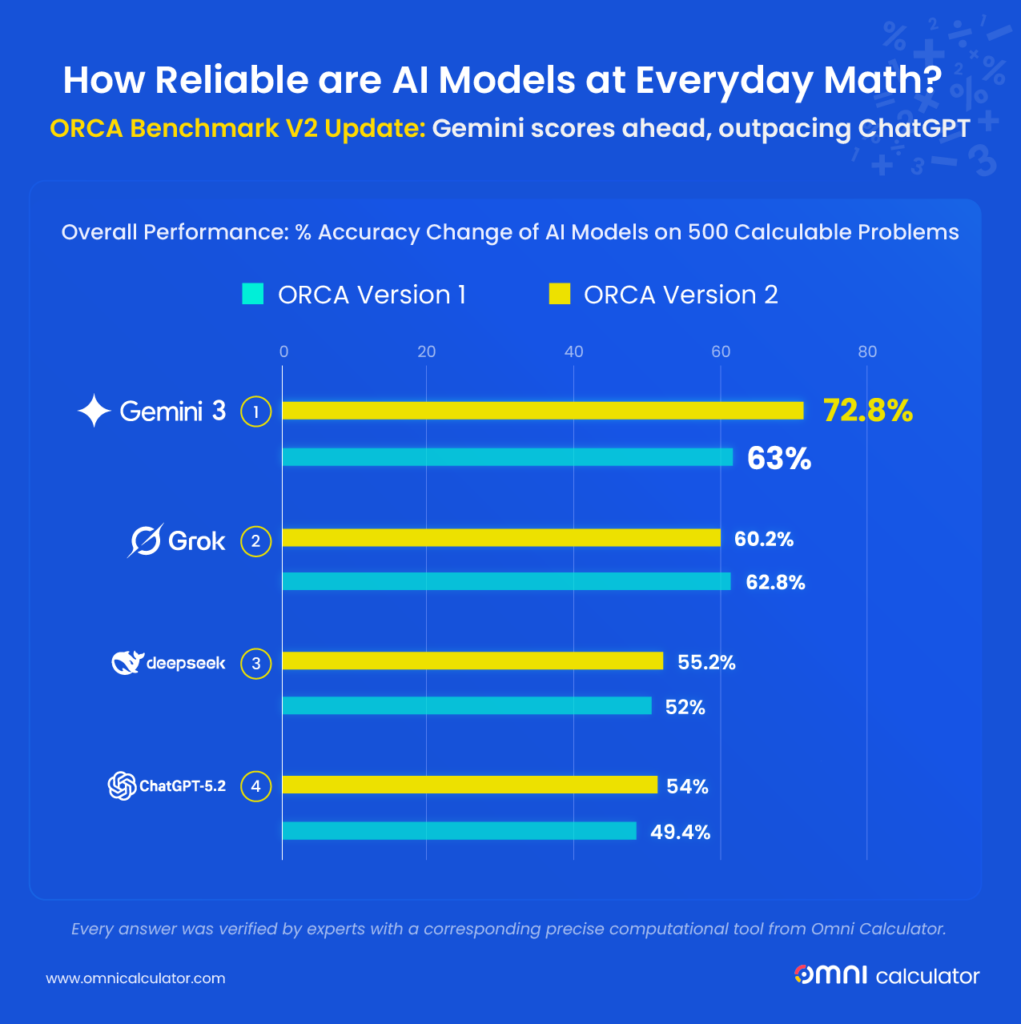
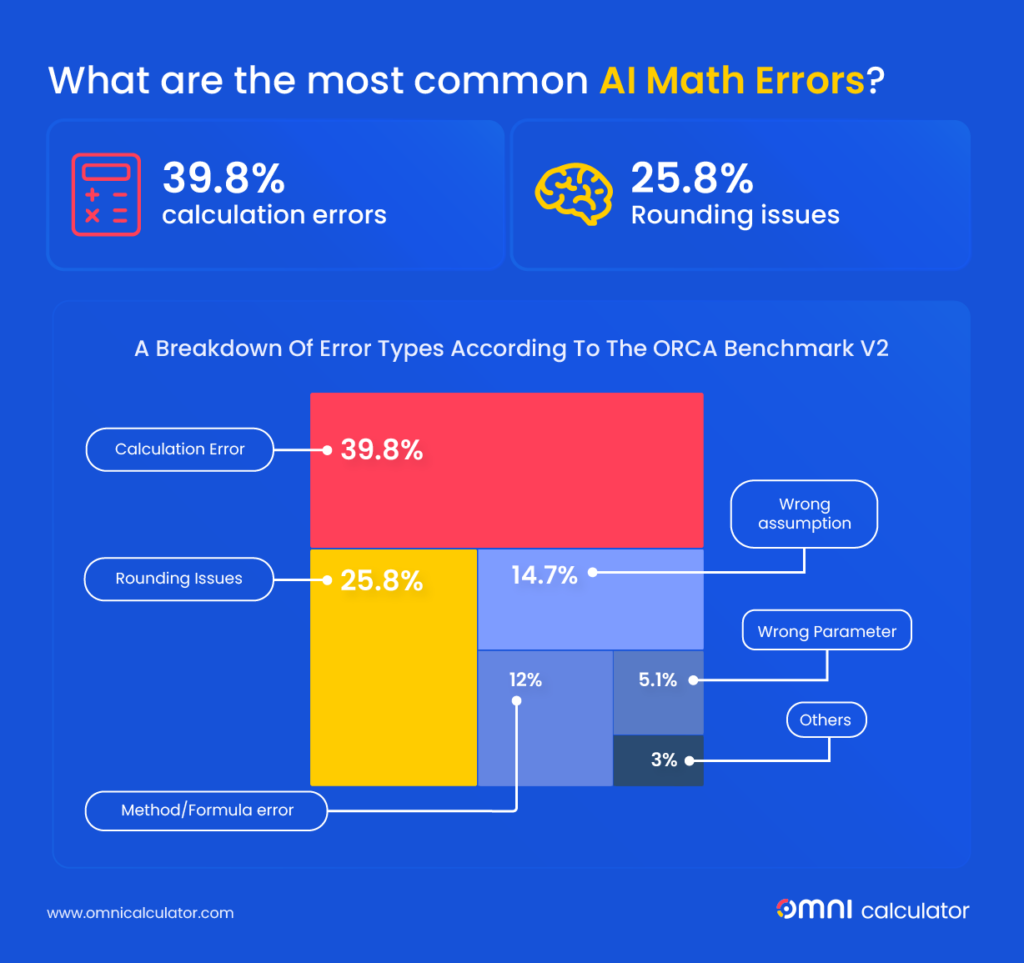
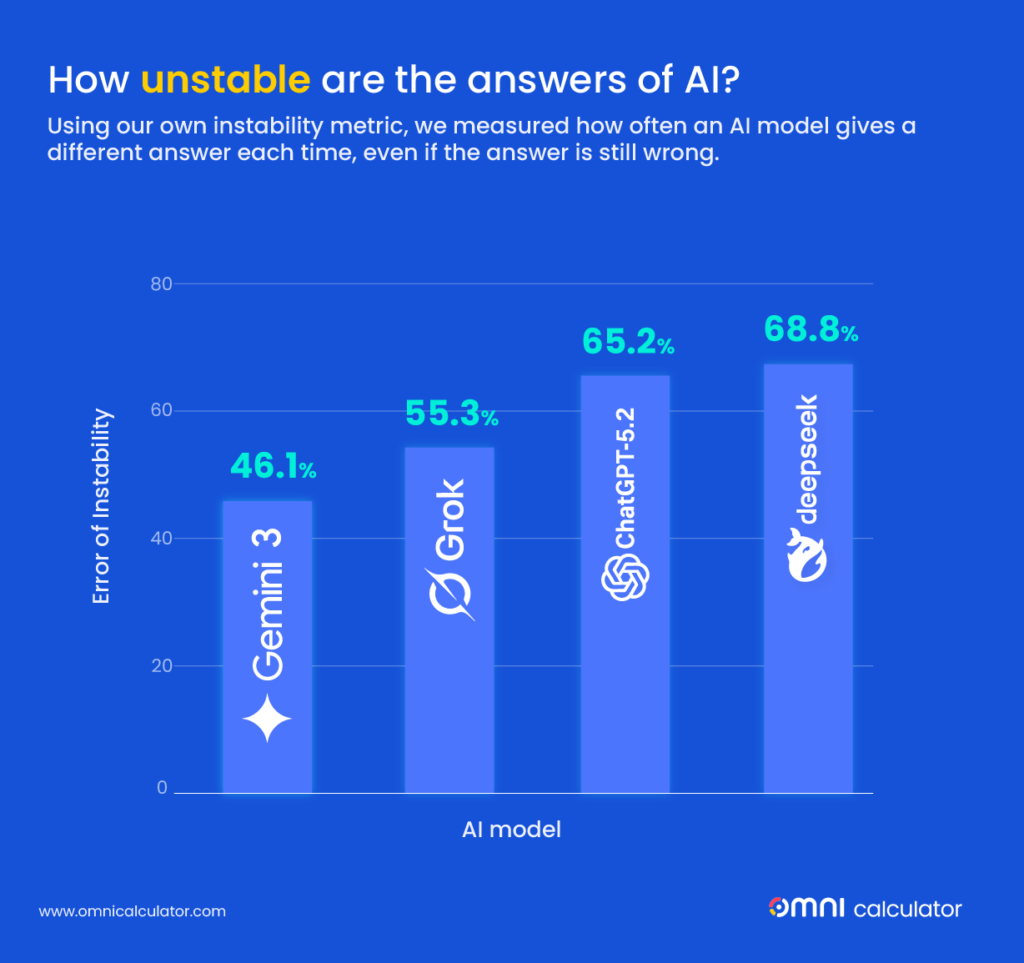
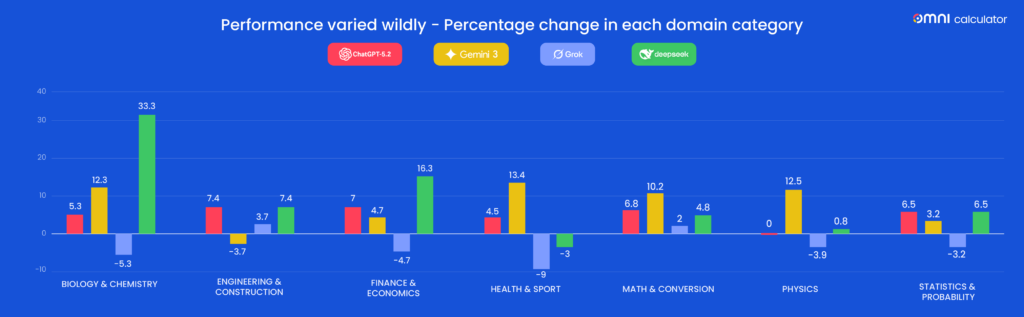
A new study introduces observed exposure, a measure that combines theoretical AI capability and real-world use to estimate which jobs are most susceptible to automation. Tasks performed by LLMs and actively automated at work receive higher exposure scores.
Computer programmers, customer service representatives, and financial analysts rank among the most exposed occupations.
The analysis finds that AI is far from reaching its full potential, with many tasks still beyond current capabilities. Occupations with higher observed exposure tend to grow more slowly, and workers in these roles are more likely to be older, female, highly educated, and earn higher wages.
Despite concerns, no systematic rise in unemployment has been detected among highly exposed workers since late 2022.
Early evidence suggests that the hiring of younger workers aged 22-25 may be slowing in highly exposed occupations. While these effects are small, they may indicate initial labour market adjustments as AI tools become more integrated into workplace tasks.
Researchers emphasise that observed exposure provides a framework for tracking AI’s economic impact over time, helping policymakers and businesses identify potential vulnerabilities.
The study underscores the gap between AI’s theoretical capabilities and actual usage, highlighting the importance of monitoring adoption patterns. The framework uses task automation and job data to track AI’s impact on the workforce.
Would you like to learn more about AI, tech and digital diplomacy? If so, ask our Diplo chatbot!