Critical internet resources
The infrastructure of the internet includes elements that are critical for it to function in a proper and stable way. These include the so-called ‘names and numbers’, that is: Internet Protocol (IP) numbers, the Domain Name System (DNS), and the internet’s root zone.
Internet Protocol numbers
IP numbers are unique numeric addresses that all devices connected to the Internet must have. Generally speaking, two devices connected to the Internet cannot have the same IP number. IP numbers are therefore the ‘addresses’ for each device.
How are IP numbers organised and distributed? The Internet Assigned Numbers Authority (IATA) – a division of the Internet Corporation for Assigned Names and Numbers (ICANN) – is the main body that distributes blocks of IP numbers to the five regional Internet registries (RIRs). The five RIRs are: AFRINIC, for Africa; APNIC, for Asia-Pacific; ARIN, for North America; LACNIC, for Latin America and the Caribbean; and RIPE NCC, for Europe, Middle East, and parts of Central Asia.
The five RIRs coordinate their activities within the Number Resource Organization (NRO), which, among others, contributes to the development of global IP number policies. RIRs distribute IP numbers to local Internet registries (LIRs) and national Internet registries (NIRs), which in turn distribute IP numbers further down the ladder to smaller ISPs, companies, and individuals.
The depletion of IPv4 and the transition to IPv6
The pool of IP numbers under IPv4, which was introduced in 1983, contains about four billion numbers. This was initially thought to be sufficient to satisfy the demand for addresses. However, in February 2011, IANA announced that it no longer had blocks of IPv4 available to allocate to RIRs. At the regional level, four of the five RIRs have also exhausted their initial pools of IPv4 addresses: APNIC in 2011, RIPE NCC in 2012, LACNIC in 2014, and ARIN in 2015.
Why has the pool of IPv4 depleted so quickly? In recent years, Internet-enabled devices, such as mobile phones, tablets, game consoles, smart assistants, and home appliances have become very popular. All of these devices require IP addresses. The developments in the area of the Internet of Things (IoT) also led to an increase in the demand for IP addresses.
How is the IPv4 depletion being tackled? The technical community developed three major actions:
- Rationalise the use of the existing pool of IP numbers through the introduction of Network Address Translation (NAT).
- Address the wasteful address allocation algorithms used by the RIRs by introducing Classless Inter-Domain Routing (CIDR).
- Introduce a new version of the TCP/IP protocol – IPv6 – which provides a much larger pool of IP numbers (over 340,000,000,000,000,000,000).
While both NAT and CIDR provided a quick fix for the shortage of IP numbers, a more sustainable long-term solution is the transition to IPv6.
How is the transition to IPv6 progressing? Although IPv6 was introduced back in 1996, its deployment has been rather slow, mainly due to lack of awareness about the need for transition, as well as limited funds for investment in new equipment in developing countries.
While internet technologies and standards allow some degree of coexistence between IPv4 and IPv6, mechanisms need to be implemented to ensure that IPv4 and IPv6 networks can properly communicate with each other, so that they do not function as islands. The Internet Engineering Task Force (IETF) has developed several specifications in this regard, outlining transition strategies, tools, and mechanisms.
The Domain Name System (DNS)
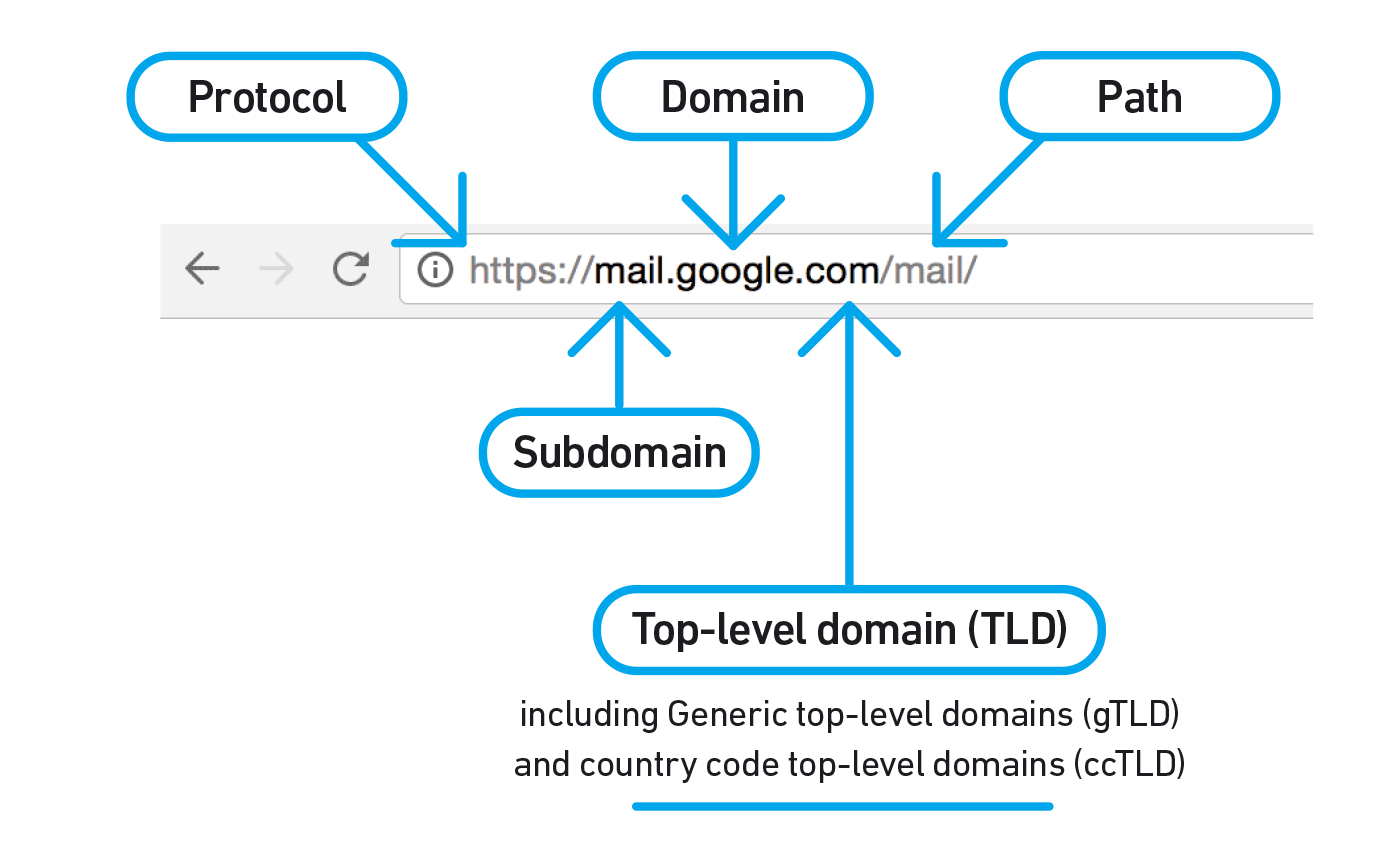
It is much easier for internet users to access websites by simply typing the domain name of the website (such as www.google.com), instead of the associated IP number (172.217.164.100 – try searching for it from your browser as if it were a URL!).
Simply put, the DNS is the system that converts domain names into Internet Protocol (IP) numbers, and vice versa. From an infrastrastructure point of view, the DNS consists of root servers, top-level domain (TLD) servers, and a large number of DNS servers located around the world.
Different types of top-level domains form part of the DNS, including generic top-level domains (gTLD) – such as .com, .net, .org, .pub, and .ngo – and country code top-level domains (ccTLD) – such as .uk for the United Kingdom, .cn for China, and .br for Brazil. Until a few years ago, only 22 gTLDs had existed. In 2012, after six years of consultations, the Internet Corporation for Assigned Names and Numbers (ICANN) launched the New gTLD Program, opening up the DNS beyond the 22 gTLDs. Internationalised domain names (IDNs) have also been introduced in recent years. For example, in China, ä¸å›½ has been introduced in addition to .cn, while in Russia, рф has been introduced in addition to .ru. IDNs are also part of ICANN’s new gTLD programme; for example, .Ñайт (website) and .онлайн (online).
How is the DNS managed? Since its creation in 1998 up until 1 October 2016, ICANN managed the DNS on a contract basis with the US government, through the National Telecommunications and Information Administration (NTIA). Abiding by this contract, the US government acted as the steward of the DNS, as every major change made within the system (such as the approval of a new gTLD) required its formal validation.
In March 2014, NTIA announced its intention to transition this stewardship role to the global multistakeholder community. As requested by NTIA, ICANN launched a process for the development of a transition proposal. At the same time, work began on elaborating a set of recommendations to enhance ICANN’s accountability towards the internet community (seen as a necessary step in the context of the transition). The work carried out by the ICANN community resulted in transition and accountability proposals, which were both accepted by the US government in June 2016.
On 1 October 2016, the IANA functions contract between the US government and ICANN expired, and the stewardship of the IANA functions was transitioned to the global multistakeholder community. In practical terms, the transition meant two major changes within ICANN: (1) the establishment of PTI as the IANA functions operator and, therefore, a more clear separation between ICANN’s technical and policymaking functions; (2) the creation of an ‘empowered community’ – mostly made up of ICANN’s advisory committees and supporting organisations – that is able to enforce a set of community powers, such as removing members of the ICANN Board and rejecting ICANN budgets or changes to ICANN bylaws.
How are domains managed? Each gTLD and ccTLD is managed by a registry, whose main responsibility is to maintain and administer a database with all registered domain names. For example, .com is managed by VeriSign, while .uk is managed by Nominet. The actual registration of domain names, by end users (called registrants) is performed though registrars. In the case of gTLDs, the registry and registrar functions are clearly separated. For some ccTLDs, the registry can also act as registrar.
Can anyone register a domain name? Yes, most gTLDs have an open registration policy, allowing the registration of domain names by any interested individual or entity. Yet, there are several gTLDs that are restricted to specific groups. For example, only authorised banking institutions can register domain names under .bank.
Regarding ccTLDs, IANA uses the principle of allocating domain names in accordance with the ISO 3166 standard for country codes. In many countries, the registry functions are then performed by public entities, private companies, or multistakeholder structures.
However, unlike the case of gTLDs, ICANN imposes no rules as to who could and how should a ccTLD be managed. ICANN goes only as far as delegating or re-delegating ccTLDs on the basis of high-level guidelines aimed at ensuring that the ccTLD registry is technically competent enough to manage it, and has support from the local community. In 2005, ICANN’s GAC adopted a set of Principles and Guidelines for the delegation and administration of country code top level domains, intended to serve as a guide to the relationship between governments, ccTLDs, and ICANN. Although some ccTLD registries (e.g. Brazil, Chile, Netherlands) have concluded some type of agreements with ICANN, and many registries are represented in ICANN’s Country Code Names Supporting Organization (ccNSO), there are several ccTLDs that have shown reluctance to become part of the ICANN system.
The root zone
The root zone is the core list of names and Internet Protocol (IP) addresses of all top-level domains – both gTLDs and ccTLDs – in the DNS. Take a look at the database of top-level domains.
The root zone is served by root servers, also known as authoritative servers, which keep a public copy of the root zone file. Globally, there are 13 main root servers, operated by 12 organisations. All the servers are replicated in multiple geographical locations through the Anycast system. Today, in fact, over 1000 servers contain copies of the root zone file. This provides many advantages, including an increased robustness of the DNS and the faster resolution of Internet addresses (with the Anycast scheme, the resolving servers are closer to the end-users).
How is the root zone managed? The management of the root zone is carried out by IANA, whose functions are currently performed by the Public Technical Identifiers (PTI), an affiliate of ICANN. In performing this role, PTI assigns the operators of top-level domains and maintains a database with their technical and administrative details.
The maintenance of the root zone file itself is performed by Verisign, on the basis of an agreement with ICANN. Verisign’s role is to edit the file (at ICANN’s proposal), publish it, and distribute it to root server operators. Prior to the IANA stewardship transition, the root zone maintainer function was the subject of a contract between Verisign and the US government.
Are there any alternative root server systems? The principle of one single root server is considered to be one of the main mantras of the Internet; any alternative root systems could lead towards the fragmentation and, perhaps even the ultimate disintegration of the Internet. Yet, alternative systems exist, and creating such a system is relatively straightforward. Examples include AlterNIC, Open NIC, New.net, Name.space, and the Yeti DNS Project.
The success of a system depends on how many followers an alternative server has, or, more precisely, how many devices on the Internet point toward it when it comes to resolving domain names. Most alternative systems have so far been unsuccessful, accounting for only a low percentage of Internet users. Without users, any alternative DNS becomes useless.